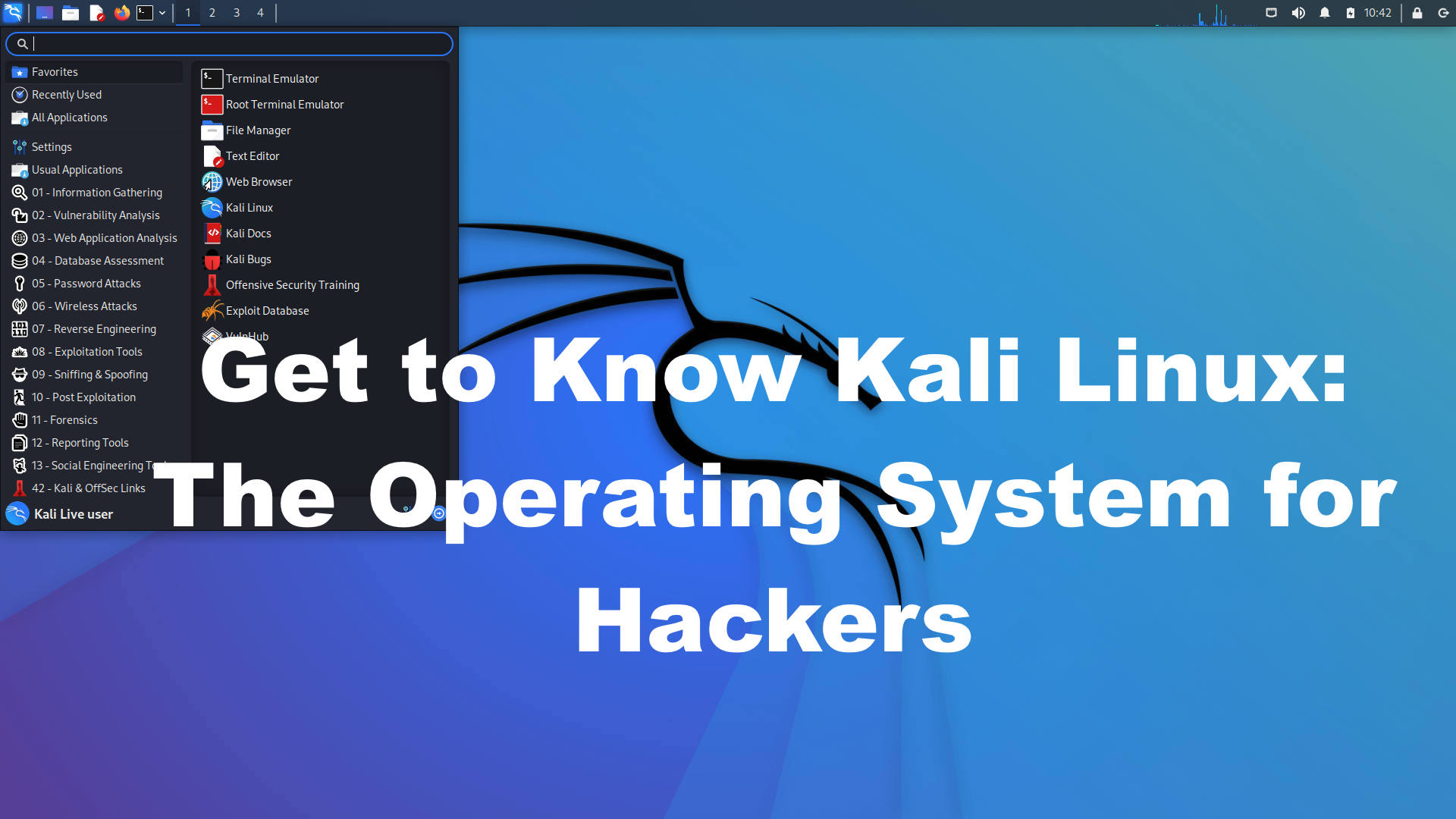
Kali Linux, previously known as BackTrack, is an operating system that you can use to hack into computers, test your network’s security and more. For beginners, Kali Linux can be daunting at first, but once you know how to navigate the open source operating system, it’s easy to use as a learning tool to develop and refine your hacking skills. In this guide on how to use Kali Linux, we will show you how to get started with the operating system, what all of its features are and how to start using it in just minutes.
What is Kali Linux?
Kali Linux is an open source operating system designed specifically for hackers, penetration testers, and security professionals. It is a Debian-based Linux distribution that comes pre-installed with hundreds of specialized tools used for testing networks and systems. Some of these tools include network mapping, vulnerability scanning, password cracking, information gathering, and exploitation.
Kali Linux was created by Offensive Security, a cybersecurity training and certification provider. The goal of Kali Linux is to provide a secure platform with the most powerful penetration testing tools available. By providing easy access to these tools, Kali Linux allows security professionals to quickly identify any security risks in a system.
Kali Linux is often used as part of a pentesting workflow. Pentesting is a type of security audit that helps organizations identify any weak spots in their systems before they are attacked by malicious actors. This process involves running various tools on the system to detect any security vulnerabilities or misconfigurations. The results of the pentest then give the organization insight into what steps need to be taken to improve their security posture.
Kali Linux provides an ideal environment for pentesting. It comes with a range of powerful tools that can be used to scan and attack systems. Additionally, it provides an easy-to-use GUI that makes using these tools straightforward. With Kali Linux, users can quickly identify any vulnerabilities in their systems and take action to address them before any damage is done.
Why was Kali Linux created?
Kali Linux is a Debian-based Linux distribution developed and maintained by the Offensive Security organization. It was originally released in 2013 and was designed with the intention of providing penetration testing and digital forensics tools for security professionals. It includes hundreds of well-known security tools, such as Metasploit, Wireshark, Aircrack-ng, and others. Kali Linux is also popular among hackers and ethical hackers due to its wide range of hacking tools and software. It is the ideal platform for anyone looking to learn more about the world of cybersecurity.
Kali Linux has been designed to help users identify weaknesses in their networks, systems, and applications. It provides a comprehensive suite of tools that can be used to test the security of various networks and systems. With Kali Linux, users can simulate attacks on a network to determine how vulnerable it is to attack, helping them identify any vulnerabilities that could be exploited. Additionally, Kali Linux allows users to collect forensic evidence and analyze it to gain insights into the system or network they are analyzing.
Kali Linux is an essential tool for those who work in the cybersecurity field, but it’s also becoming increasingly popular among hobbyists who want to learn more about hacking and digital forensics. It offers an abundance of features that make it a great platform for anyone interested in learning more about the world of cybersecurity.
Who uses Kali Linux?
Kali Linux is a Debian-based operating system designed for digital forensics and penetration testing. It is developed and maintained by Offensive Security and was released back in 2013. Kali Linux is a popular choice among ethical hackers, security researchers, and pentesters who use it to perform various tasks such as vulnerability assessment, network analysis, security auditing, and more.
Kali Linux is packed with hundreds of pre-installed tools for penetration testing and digital forensics. Some of the popular tools include Wireshark, Aircrack-ng, Nmap, Metasploit Framework, and John the Ripper. With these powerful tools, Kali Linux allows users to easily identify and exploit vulnerabilities in systems or networks.
Kali Linux also provides users with an extensive collection of resources for learning about hacking and security related topics. The official website contains tutorials, videos, blogs, and other useful information that will help users improve their knowledge and skills in the security field. Additionally, Kali Linux has a huge community of users who are always willing to help and answer questions related to its usage.
Overall, Kali Linux is a great operating system for those who want to learn more about digital forensics, hacking, and pentesting. If you’re looking for an easy way to get started with security research and testing, then Kali Linux might be the right choice for you!
What are the features of Kali Linux?
Kali Linux is a powerful, open-source operating system specifically designed for ethical hacking and penetration testing. It provides users with a wide range of security tools that can be used to detect, prevent, and mitigate security threats. Its primary focus is to help hackers identify and exploit vulnerabilities in computer systems.
Kali Linux is based on the Debian distribution and comes with many pre-installed security tools like Metasploit, Nmap, Wireshark, Aircrack-ng, Burp Suite, and more. The operating system also includes various tools such as a full-featured web application scanner, password cracker, packet sniffers, and exploitation tools.
Kali Linux has several advantages for ethical hackers. For example, it provides an easy-to-use interface with access to numerous security tools that are available on its repository. Additionally, the operating system offers enhanced anonymity features such as TOR and VPN support. Furthermore, Kali Linux supports a wide range of architectures, including ARM and virtualization platforms.
Overall, Kali Linux is an essential tool for ethical hackers who want to test their skills and protect their networks from potential threats. With its comprehensive security tools and advanced features, it is no wonder why Kali Linux is the most popular choice among experienced hackers.
System Requirements for Kali Linux
Kali Linux is a powerful and feature-rich operating system that is primarily used for digital forensics and penetration testing. Before you get started with Kali Linux, it’s important to understand the system requirements.
The minimum hardware requirements for running Kali Linux are an Intel x86 processor with 512 MB of RAM, and at least 8 GB of hard drive space. For virtual machines, Kali Linux supports both VirtualBox and VMware. You’ll need to make sure that you have enough RAM and hard drive space to allocate to Kali Linux, as well as an internet connection for installing packages.
Kali Linux can be installed on a variety of platforms, including Mac OS X, Microsoft Windows, and other versions of Linux. If you are running a version of Linux other than Debian, you may need to configure your package manager in order to install Kali Linux.
Once your system is configured and ready to go, you can install Kali Linux using one of several methods, including network installation and disk cloning. Once you’ve got the system up and running, you’ll want to start exploring the range of tools that Kali Linux has to offer.
Kali Linux is a powerful and useful tool for security professionals, and understanding the system requirements is essential for getting the most out of your experience. With the right setup, you can make sure that you get the most out of your time with Kali Linux.
How do I install Kali Linux?
Installing Kali Linux is a relatively straightforward process and can be done in just a few simple steps. Before you get started, make sure you have at least 8GB of free disk space and an internet connection available.
First, download the latest version of Kali Linux from its official website. Once you’ve downloaded the ISO image file, burn it to a DVD or create a bootable USB drive using UNetbootin or another compatible tool.
Once your media is ready, insert it into your computer and restart the system. During the bootup process, make sure to select the option that says Install Kali Linux. After a few minutes of setup, you’ll be able to select your preferred language and set up your username and password.
Once all of this is complete, Kali Linux will be installed and ready to use. You can now begin exploring its many features and tools, including an extensive suite of hacking and security tools specifically designed for ethical hackers. With Kali Linux, you have everything you need to start learning about ethical hacking and cybersecurity.
How do I use Kali Linux?
Kali Linux is an open source operating system specifically designed for security testing, digital forensics, and penetration testing. It is a Debian-based Linux distribution with a large collection of security-related tools and services. Originally released in 2013 by Offensive Security, Kali Linux is one of the most popular and widely used distributions among hackers, security professionals, and IT professionals alike.
Kali Linux is incredibly versatile and can be used for a variety of tasks. Whether you're a seasoned hacker or just getting started, it's essential to have a basic understanding of how to use Kali Linux. Here are some ways you can get the most out of your Kali Linux experience:
What are some of the most popular hacking tools in Kali Linux?
Kali Linux is an open-source operating system designed for digital forensics and penetration testing. It is the most popular OS for ethical hackers due to its comprehensive tools for network scanning, wireless analysis, and exploit development. Kali Linux comes pre-installed with hundreds of security tools, including some of the most popular hacking tools used by professionals today.
Some of the most popular hacking tools in Kali Linux include:
Nmap – Nmap (Network Mapper) is a powerful tool for scanning networks and discovering hosts. It can also be used to discover vulnerable services running on a target system.
Metasploit – Metasploit is a powerful exploitation framework used to create and execute exploits against remote systems. It has been integrated into Kali Linux and allows users to perform advanced attacks such as buffer overflow and reverse shells.
John the Ripper – John the Ripper is a popular password cracking tool that can be used to recover forgotten passwords from a variety of systems and file formats.
Wireshark – Wireshark is now a powerful packet analyzer which is used for network troubleshooting and analysis. It is able to capture and decode data on a network, allowing users to examine traffic and detect malicious activity.
Aircrack-ng – Aircrack-ng is a suite of tools for cracking WiFi networks. It can be used to test a network’s security and crack WEP or WPA keys.
These are just a few of the powerful hacking tools included in Kali Linux. With its wide range of security tools, Kali Linux is the perfect choice for anyone looking to explore the world of ethical hacking and penetration testing.
Are there any security risks associated with using Kali Linux?
Kali Linux is one of the most popular operating systems used by hackers and cybersecurity professionals alike. Despite its immense popularity, however, there are still some security risks associated with using Kali Linux. This article will explore these potential risks and provide tips for keeping your system safe.
The most common risk associated with using Kali Linux is the fact that it contains numerous open-source tools that can be used for malicious purposes. While many of these tools can be used for legitimate tasks, hackers can use them to gain access to systems or launch attacks. As a result, it is important to make sure that you only install applications that you trust and that you update the system regularly to ensure that all security patches are applied.
In addition, the default settings on Kali Linux are not always secure. In order to make sure that your system is as secure as possible, you should consider changing the default password, disabling unnecessary services, and running regular scans with updated antivirus software.
Finally, it is important to remember that Kali Linux is designed for hacking, so it is essential to practice good online hygiene when using it. Be aware of phishing attempts, malicious links, and other online threats, and never download suspicious files or programs without proper verification.
By taking the necessary precautions, you can protect yourself from the security risks associated with using Kali Linux. Keep in mind that the system is designed for hacking, so be sure to use it responsibly and keep your system up-to-date to stay safe.
How can I learn more about Kali Linux?
Kali Linux is an open-source operating system designed specifically for network security, digital forensics, and penetration testing. It is based on the Debian Linux distribution and is maintained and funded by Offensive Security, a leading information security training company.
Kali Linux has become the de facto standard operating system used by ethical hackers and security professionals. Its vast collection of tools, combined with its robustness and ease of use make it the perfect choice for carrying out ethical hacking tasks.
Kali Linux contains hundreds of open-source tools for performing various types of reconnaissance, vulnerability scanning, exploitation, and post-exploitation attacks. The main objective behind its development was to provide a platform for pentesters to test their skills and tools in a safe environment.
Kali Linux also includes a wide range of security tools for carrying out various network-related tasks such as network mapping, port scanning, password cracking, remote exploitation, and much more. It is frequently updated and comes with a clean and easy-to-use interface that makes it the go-to platform for anyone looking to improve their ethical hacking skills.
For those looking to learn more about Kali Linux and its many capabilities, there are a number of online resources available. There are tutorials, guides, blogs, and forums dedicated to teaching users how to use the tools included in Kali Linux, as well as how to set up and configure the operating system for optimal performance. Additionally, there are a number of bootcamps and training courses available for those who want to take their knowledge of Kali Linux to the next level.
FAQ=======================
Is kali Linux normal to use or it is illigal?
Kali Linux is a powerful open-source operating system that is often used by ethical hackers and penetration testers. It is legal to use Kali Linux, as long as you use it responsibly and only for security testing. It is not intended to be used for illegal activities such as malicious hacking or creating malware. Kali Linux is a great tool to help security professionals identify security flaws and find solutions to protect networks and systems from possible attacks. It is important to remember that Kali Linux should be used in accordance with all applicable laws and regulations.
Is it safe to use Kali Linux in normal computer?
Kali Linux is an open-source operating system designed for digital forensics and penetration testing. It is based on Debian Linux, and comes pre-installed with a variety of security tools such as Metasploit, Nmap, and Wireshark. With its wide range of capabilities, Kali Linux is often used by ethical hackers and cybersecurity experts to test networks and systems for vulnerabilities.
When it comes to using Kali Linux in a normal computer environment, the answer is yes - it is safe to use. However, given the nature of its purpose, you should be extra careful while using it. It is essential that you follow the instructions provided with Kali Linux and use it only for legitimate activities. Additionally, you should always keep your system updated and run regular vulnerability scans to ensure your system remains secure.
As with any other operating system, you should be aware of the risks associated with running Kali Linux on your computer. While it is designed for use in secure environments, it could be subject to malicious attacks if left exposed. It is also important to remember that Kali Linux was created for ethical hacking and penetration testing and should not be used for any illegal activity.
Overall, Kali Linux is a powerful and secure operating system that can be used safely in a normal computer environment. If you are careful to follow all instructions and precautions, then you can benefit from its wide range of features without worrying about compromising your system’s security.
Is Kali good for gaming?
When it comes to gaming, Kali Linux is not the best choice for most users. However, for some gamers, it may be the perfect solution for their needs. As the operating system of choice for hackers, Kali Linux is designed with a focus on security, not gaming performance. It has many powerful tools for penetration testing, digital forensics, and reverse engineering, but lacks the support for high-end gaming capabilities. That being said, if you are looking for a lightweight and secure system that allows you to do your gaming without too many performance issues, then Kali Linux might be the way to go.
For those who are looking for a reliable operating system for gaming, there are plenty of other options available. Windows and MacOS are the two most popular choices, but there are also various Linux distributions such as Ubuntu and Mint that provide good performance while still offering robust security. So if you're looking for a secure and reliable operating system to game on, consider giving Kali Linux a try.
Thank you
If you have any questions or would like more information on how to use Kali Linux, please feel free to reach out to us. We are more than happy to answer any questions you may have about this powerful operating system.
Again, thank you for reading our post. We hope you have a great day!
Keywords:
- Kali Linux
- operating system
- BackTrack






Leave a comment